
Table of contents
1. Introduction
As per reports, the global average cost of data breaches in 2023 stood at USD 4.45 million, and the global annual cost of cybercrime is estimated to reach USD 9.5 trillion in 2024. That’s the heavy, heavy cost organisations worldwide have to suffer along with reputational losses because a hacker somewhere decides to breach data for their benefit.
With more and more technologies emerging, cyberattacks are, unfortunately, also on the rise. It is not just scamming messages or phishing attempts – the circle is much bigger than one can think. Such crimes have been on the rise in organisations dealing with technologies and data at the maximum. But, to think that cybercrimes are limited to only tech companies would be an understatement. In our previous cyberattack blog, we have spoken about the various industries where a luxury cosmetic brand, a legal organisation, and an entire government, where cybercrimes penetrated.
1.1 The staggering cost of ERP system breaches
Organisations rely on Enterprise Resource Planning i.e., ERP systems to empower their businesses, manage product lifecycle, critical processes, etc., ensuring a continuous and open flow of information.
In 2018, US-CERT warned organisations globally about the cybercrimes targeting ERP applications while Reuters reported that several systems across various industries were hit after they failed patch installations. With the number of cyberthreat actors today, the ERP systems attacks mainly targets cyber espionage and sabotage – a high-profile example of which is the United States Information Service (USIS) breach.
For you and me, ERP systems are to ensure smooth and seamless business operations. But for cyber-criminals, such systems are a way of disrupting operations to gain monetary benefits from the breach. And it is quite a simple logic why cybercriminals attack these systems – ERPs contain sensitive and business-critical data.
So how does one ensure that their ERP systems or entire IT landscape, for that matter, are protected from such malicious cyberattacks and cybercriminals? An effective answer here would be – Threat Prevention!

2. What is threat prevention?
In network and enterprise security, threat prevention refers to the policies and solutions that protect your corporate network. In the past, it primarily focused on the perimeter while relying extensively on traditional antivirus and firewalls. However, with the increasing range of threats like malware, ransomware, and so on, corporate networks require an integrated, multilayered approach to security. And it is not just outdated operating systems that make a way for cybercriminals to target the systems. Many times, software vulnerabilities, especially legacy systems, are causes of network security attacks.
In such cases, tools for intrusion threat detection and prevention have become a necessity in the corporate cybersecurity landscape. The threat prevention suite comes with multiple layers of cyber tools, where network threat prevention, endpoint prevention, and predictive malware protection are a few common points.
3. Importance of threat prevention
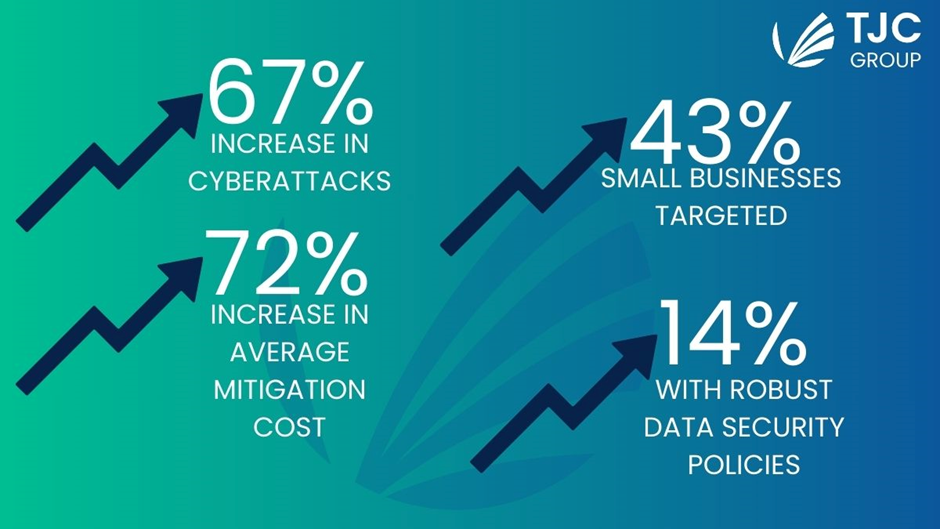
Studies show an alarming number of cyberattack frequencies on businesses and the cost they have to bear due to the breach. According to a 2019 study by Accenture in collaboration with the Ponemon Institute, it is stated that there has been a 67% increase in data breaches over the last five to seven years. Additionally, the average mitigation cost too increased by a massive 72% over the same period. A myth goes around of cybercriminals attacking large corporations the most as they have invaluable information. Busting that myth, Accenture’s report found that 43% of cyberattacks target small businesses, with only 14% having robust security to protect their data.
The Ponemon Institute also published a separate report on the State of Cybersecurity in 2019 stating their discovery that 45% of small and medium-sized businesses consider their cyber policies and solutions ineffective in case of cyberattacks. What’s more surprising is that 66% of the respondents were targets of cyberattacks just 12 months before the survey.
In 2017, Steve Morgan of Cybersecurity Ventures, predicted that by 2021, every 11 seconds a cyberattack will take place. It is 2024, and we know the severity and frequencies of these attacks – from small businesses to large corporations (Google, X, Meta, LinkedIn, Infosys, etc.), every tech landscape has been the victim of hackers. Unfortunately, a 100% immunity for cyberattacks isn’t possible as of yet, but some measures prevent a majority of the attacks on corporate networks. We have to act now and the importance of threat prevention for your ERP systems cannot be stressed enough.

4. Protect your ERP systems with SAP Enterprise Threat Detection
According to Forbes, just a few years ago, ERPs were viewed as a way to segregate duties effectively – which means preventing cyber cases where an employee was solely responsible for one task. However, the scenario has completely changed over time, and now leading analysts say that ERP security is a topic to watch as attacks due to critical vulnerabilities on these systems hit the headlines regularly. I have to stress here that ERP security is not a brand-new topic, but the concept has significantly evolved over the years.
For those with ERP systems from SAP, the good news is that the company released SAP Enterprise Threat Detection to help protect against malicious attacks. It is a real-time, cloud-based enterprise threat detection solution customised for SAP applications, delivered and managed on the SAP Business Technology Platform. The solution aims to support its customers and partners in detecting cyberattacks in real time by collecting, correlating, and analysing abnormal and suspicious events across the SAP landscape.
4.1 The concept behind launching SAP Enterprise Threat Detection
By 2027, the older ERP systems will be discontinued, leaving companies with the option to migrate to the cloud or SAP S/4HANA. The migration is a blessing in disguise as it allows organisations to enhance their corporate network’s security measures. Today, data security and privacy are of the utmost importance, and failing to make them a priority means risking your network, possibly facing hefty consequences in the future.
Notably, cyberattacks against businesses are daily news. But have you noticed that little technical details are shared about the layers of the IT landscape being attacked? Since your ERP systems contain confidential and sensitive data, running the most critical process across the enterprise, they are becoming an interesting and high-value target for cybercriminals. While the security teams are standing guard at the core, cybercriminals are making strategies to penetrate the organisation’s crown through application layers. SAP Enterprise Threat Detection aims to detect any malicious attempts made on the ERP systems, raising alerts faster with SAP customers and partners.
5. Prevent malicious threats with legacy system decommissioning
Other than the enterprise threat detection solution, what cost-effective measures can be taken to protect your old ERP systems and applications? The answer is legacy system decommissioning! As mentioned earlier, regular and updated patches are mandatory; unpatched systems are one of the easiest ways for cybercriminals to gain access to ERP systems – they target system flaws and vulnerabilities.
System patching needs attention and becomes complicated when legacy data is lingering around. Legacy data (systems)are a high cybersecurity risk because they might not be encrypted or protected by access controls. Arguably, this leads to making the legacy systems more vulnerable to breaches and cyberattacks.
Decommissioning of legacy data and systems can be a tedious and complicated process. To decide which data is important and which to discard as legacy, especially in highly regulated sectors like finance or healthcare or during audits. One way would be to decommission the legacy data and store it away from the other critical databases – preferably in a place where cybercriminals will not be able to gain access. But again, the question arises – where? ELSA (Enterprise Legacy System Applications) is a good option.
Designed and developed by TJC Group, it neatly ring-fences obsolete data while maintaining its smooth and easy accessibility. In terms of security, ELSA is built on SAP BTP (the same platform where the SAP Enterprise Threat Detection is managed). Additionally, the application is connected to a database (such as MySQL, PostgreSQL or HANA Cloud) and BLOB storage with a private endpoint connection. One of the best features of ELSA is that it’s an SAP native application, designed to be use with SAP systems but equally compatible with non-SAP legacy systems. ELSA ensures all legacy data is stored securely, minimising any risk from cybercriminals, and benefiting from both SAP and major hyperscaler security measures.

Not to forget, TJC Group has received the ISO Certification 27001 bestowed to companies that have put in place a robust Information Security Management System, certifying our efforts to ensure a solid cyber landscape for our employees and customers.
Contact us today for more information on ELSA and keep your ERP systems protected from malicious threats.







