
Table of contents
- What is a cyberattack?
- Dangers of cyberattacks
- Types of cyberattack and threats
- Types of cyberthreat actors
- Emerging cyberattacks to look out for
- Legacy system decommissioning: A way to prevent cyberattacks
- A word from the Director of IT Security, TJC Group
- Severity of the cyberattacks
- Best practices to follow
- Key takeaways
“Luxury cosmetic brand Estee Lauder faces a cyberattack [1] causing disruption to business operations”.
Quinn Emanuel confirmed to Reuters [2] on Monday that “a third-party data centre we use for document management for some of our clients became the victim of a ransomware attack”.
“A single Indian organisation suffered 2,146 cyberattacks on average [3] per week in the last six months, compared to 1,239 attacks per organisation globally”.
“Twelve Norwegian government ministries have been hit by a cyberattack, the Norwegian government [4] said on Monday, the latest attack to hit the public sector of Europe’s largest gas supplier and NATO’s northernmost member”.
And many more that goes unreported.
Over the last couple of years, the number of data breaches have been on the rise, with no signs of slowing down. These breaches have affected organisations of all sizes and sectors across the globe. As you can see in the examples above, cyberattacks have penetrated through a luxury cosmetic brand, a legal organisation, tech companies, and through an entire Government – the damages being enormous, costing millions in terms of money. As a matter of fact, according to a report by Cybersecurity Ventures [5], the global annual cost of cybercrime is predicted to cross $8 trillion – the number can, of course, go beyond this. Apart from causing financial damages, cyberattacks also lead to regulatory penalties, lawsuits, business continuity disruptions, and severe reputational damages.
According to the 2020 Data Breach Investigations Report by Verizon, 86% of cybersecurity breaches were financially motivated while 10% were motivated by espionage. However, does the motivation behind these attacks matter? Business disruption, corporate espionage, financial gain, or whatever the motivation is, cybersecurity threats have become omnipresent that continues to disrupt and capsize every facet of the digital world.
Knowing about cyberattacks, its types, severity, and so on, is quintessential in today’s era. To help you out with the same, our in-house experts have created a detailed blog on knowing A-Z about cyberattacks. Read on!
What is a cyberattack?
Simply put, a cyberattack is an attempt by cybercriminals, hackers, or other digital adversaries, like hacktivists, to access a computer network or system, usually for the purpose of altering, stealing, destroying, or exposing information. Cyberattacks can be launched from any location, which are performed by an individual or a group, using one or more tactics, techniques, and procedures (TTPs).
The most common terminology used to refer the ones behind cyberattacks is hackers; however, they are also known as cybercriminals, threat, or bad actors. Cybercriminals work alone or as a part of organised criminal groups; they also collaborate with other hackers to launch cyberattacks. Hackers usually identify vulnerabilities, like weaknesses in the computer system, and exploit them for their goals.
Dangers of cyberattacks
Cyberattacks have destructive and dangerous consequences on both businesses and individuals. A hacker not just targets an organisation, but also individuals at home. Here are how these attacks work in business and at home –
1) Cyberattacks in businesses
A cybercriminal hacks a business to obtain the company’s financial data, client list, or any other data like – customer data, intellectual property, proprietary information, and personally identifiable information (PII). However, in some cases, such attacks are launched simply to disrupt business operations. Cyberthreats impacts businesses negatively in the form of lost and stolen data, downtime during recover, and most vigorously – the loss of consumer trust in cases where PII has been stolen. Apart from this, recovering from a data breach is financially straining for businesses – it is not just restoring networks but also repairing reputational damage. Figure wise, according to IBM’s Cost of a Data Breach 2023 report, recovering from cyberattacks estimates an average at $4.45 million.
2) Cyberattacks at home
Cybercriminals don’t limit their attacks to businesses – they attack individuals at home too; the impact being equally damaging. Again, such attacks result in stolen data, financial information, and compromised devices, cause a network or system to shut down, and so on. Hackers usually target stealing personal identifiable information (PII) to resell them on dark web or impersonate the target to trick their friends and family into sending money.
Types of cyberattack and threats
When types of cyberattacks and threats are spoken of, phishing, malware, or in general, the term ‘hacking’ comes to our minds, isn’t it? However, you will be surprised to know that there are approximately 10 types of cyberthreats, with more on the rise. Here are the top ten cyberthreats that you must be aware of –
1) Malware
One of the most common cyber security threats, malware is a malicious software, a virus, or a worm that gets installed into the system when the user clicks on a dangerous link or email. Once it installs into the system, malware blocks the access to critical components of the network, damage the system, gather confidential information, wipe files critical for operation, and so on. Malware has several forms, which includes –
Trojan Horses: In general, the term “Trojan Horses” may be associated with the Greek Trojan War, but when it comes to cybersecurity – Trojan Horses is a type of malware threat, where the virus disguise itself as a program or hide within legitimate software to trick users into installing them. A remote access Trojan or RAT creates a secret pathway on the device while a dropper Trojan installs additional malware.
Spyware: A common type of malware threat, spyware secretly gathers sensitive information like credit card numbers, login credentials, and so on, which then sends these details back to the hacker.
Scareware: This malware takes the help of fake messages to scare victims into downloading the virus while passing sensitive information to a fraudster.
Worms: These are self-replicating malicious codes that can spread between apps and devices automatically.
Rootkits: Rootkits are malware packages, giving hackers administrator level access to a computer’s operating system or any other assets.
2) Phishing
Phishing is known to be the most pervasive social engineering attacks and the second most cause of breaches. In this, cybercriminals send malicious emails using details that looks like legitimate sources. The mention of the legitimate resource tricks the user into clicking the malicious link in the email, which leads to the installation of malware, viruses, or disclosure of sensitive information like credit card details, login credentials, and so on. Apart from emails, cybercriminals phish using text messages, social media portals, and through IVR calls.
So how do you identify which is a legitimate source and which one’s not? Here’s an example below:
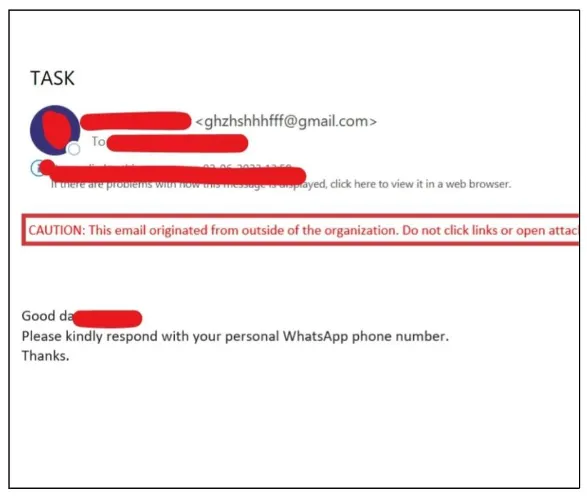
This phishing email was sent to an employee of an organisation, using the name of the CEO.
Consider the name of the organisation to be XYZ and the name of the CEO to be Lorem Ipsum. An official email is sent using the official email address, which for the XYZ organisation should be lipsum@xyz.com.
However, if you see the image, email id is a bunch of syllables followed by a Google domain. The email address itself is a big red flag to know that this is a phishing scam.
These minute details go unnoticed, and employees usually give in to the scammers demands unknowingly. It is always a good practice to check the details before reading or clicking on the content and links of the email and text messages.
That said, for fake calls through IVR or normal phone numbers, if the caller asks for your PIN, card CVV, OTP, and so on, simply block the number. Remember, no bank, financial institution, or any legit person, for that matter, will never ask you these personal details.
3) Spear Phishing
Apart from the standard phishing practices, cybercriminals also practice its more sophisticated form known as ‘Spear Phishing’.
Spear Phishing specifically targets high-level C-suite executives, system administrators, and other such authorised users of an organisation. Such cases are known as business email compromise (BEC) fraud, in which cybercriminals disguise as vendors, executives, or business associates, tricking victims into sharing sensitive data or wiring money.
4) DNS attack
A type of cyberattack that targets the Domain Name System (DNS); it exploits the vulnerabilities in the DNS to divert site visitors to malicious pages and remove data from the compromised system. The diversion of visitors to illegitimate or fake pages is known as DNS Hijacking while the removal of data is known as DNS Tunnelling.
DNS is important for various networked applications, which includes email, web browsing, e-commerce, etc., making organisations vulnerable to cyberattacks. According to a 2020 Global DNS Threat Report, nearly 79% of the surveyed organisations experienced DNS cyberattacks, with each of the attack averaging to USD 924,000.
Another challenge with the DNS landscape is the adoption of cloud-based DNS. Although, the shift from traditional to cloud-based DNS enhanced flexibility and domain performance for better user experience, it has also resulted in several security threats like Zero-day attacks and Distributed Denial-of-Service (DDoS). That said, the number of business-critical applications hosted in hybrid-cloud environment also increased, enabling cybercriminals to target the cloud easily.
As per the same Global DNS Threat Report, companies experienced cloud service downtime increased from 41% in 2019 to 50% in 2020. Moreover, 82% of the surveyed organisations experienced application downtime due to the DNS attacks – both on-premises or in the cloud. The report also revealed that the in-house application downtime surged as well.
The consequences of DNS attacks are extremely draining – both financially and reputationally, directly impacting the business continuity. Therefore, ensuring a secured DNS service availability and integrity must become a priority for organisations.
5) Distributed Denial of Service (DDoS)
Distributed denial of service or DDoS attacks are a broader category of the denial of service (DoS) attacks. DoS attacks, in general, include cyberattacks that slow or stop applications and network services.
DDoS precisely attacks to disable or disrupt a website, cloud service, web application, or any other online resources by injecting it with pointless connection requests, malicious traffic, or fake packets. This overwhelms the connection, slowing down the target to crash altogether, making it unavailable to the authorised/legitimate users. Another thing about DDoS is that they send attack traffic at once from multiple sources. Cybercriminals have been using DDoS attack for more than 20 years; however, it has spiked tremendously in recent times. According to a report, the year 2019 witness around 8.4 million DDoS attacks, and there was an increase of 203% in the first half of 2022.
In this distributed denial of service attacks, cybercriminals first select the targets, which are usually online retailers, cloud service providers, financial institutions, gaming companies, and Software-as-a-Service (SaaS) providers. Then, they create a botnet by either renting or buying them. Botnet is a network of internet connected devices, infected with malware, allowing hackers to control the devices remotely. Finally, cybercriminals launch the attack by commanding the devices in the botnet to send packets or connection requests to the IP address if the targeted server, device, or service.
Hence, it is imperative for organisations or even as individuals to be aware of clicking on URLs or messages that you feel are remotely suspicious.
6) Ransomware
A type of malware, ransomware attacks encrypt and locks the victim’s data while threatening to publish or block the authorised access unless a hefty ransom is paid. However, even after paying the ransom, there is no guarantee that you will regain the access to the system. One can tout it to be a costly gamble with severe consequences on the company or the individual’s future. There are three ways in which the malicious software prevents access –
- · User file encryption
- · Remote access and control of the victim’s system
- · User screen lockdown
Once the malware penetrates through, it spreads all over the networked system and encrypts the data. After which, the attacked system displays a ransom note, which demands a hefty amount in exchange for the decryption key while threatening the user of dire consequences.
Apart from this, ransomware can also enter the systems through an exploit kit that controls security vulnerabilities in the servers. A classic example of such a ransomware attack is WannaCry that penetrated hundreds of systems globally through a gaping security hole in the Microsoft Windows OS in 2018.
As per the report of The State of Ransomware 2020, malicious documents, attachments, etc., accounted for 29% of ransomware attacks while remote attacks on server accounts accounted for 21%. According to the same report –
- · 56% got their data back through backups without having to pay the ransom.
- · 26% of the victims had to pay the ransom and got their data back.
- · 1% paid the ransom, however, did not get their data back.
Ransomware attacks sometimes pass off a software update – after installation, it creates havoc upon the system. Hence, update your systems only when your system (Samsung, Lenovo, Dell, Apple) or the IT administrator gives the prompt.
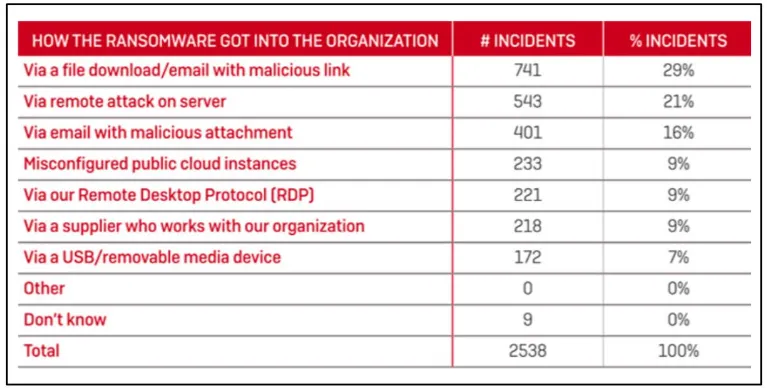
Source: Ransomware Threat: All You Need To Know! (stealthlabs.com)
7) Advanced Persistent Threats (APT)
A unique breed of cyberattacks, Advanced Persistent Threats or APTs can infiltrate an organisation’s network while maintaining ongoing access over a long period of time. This type of cyberattack employs sophisticated techniques to gain initial access, often by exploiting vulnerabilities in the systems or through phishing attacks. Once penetrated, APT attacks silently work to achieve their targets – data theft, disrupting business operations, and so on.
8) SQL Injection
A Structured Query Language or SQL injection is a type of cyberattack where cybercriminals attempt the access to the database by uploading malicious SQL scripts. Once successful, the cybercriminals can view, change, or delete the data in the SQL database as an attempt to disrupt business operations or steal data. It is reported that SQL Injection accounts approximately 65% of all the web application attacks.
Apart from these eight types of cyberattacks, the other two major attacks are – Zero-day exploit and Man in the Middle (MTM) attacks.
Types of cyberthreat actors
Cybersecurity breaches have actors that launches these attacks to achieve their objective. In order to securing your networks, systems, etc., and ensuring effective response in case of a breach, knowing the type of cyberthreat actor is crucial. Here are the seven cyberthreat actors that you must be aware of –
1) Nation states
Nation states are cyberthreat actors from unfriendly/conflict nations that can cause detrimental impact by creating disruption in communications, military activities, and everyday life.
2) Hackers
Hackers are one of the most notorious cyberthreat actors that explore several cyber techniques to breach security while exploiting vulnerabilities in a computer system or network. Hackers usually attack for revenge, personal gain, financial gain, stalking, and political activism.
3) Criminal groups
Criminal groups are cyberthreat actors that attacks a system or network for financial gains. They use spamming, spyware, phishing, and malware to achieve their objectives and conduct online fraud, identity theft, and system extortion.
4) Hacktivists
These are cyberthreat actors that carry out cyberattacks for political cases instead for financial or personal gains. They target organisations, industries, or individuals that don’t align with their political agenda and ideas.
5) Terrorist groups
Another notorious cyberthreat actors, terrorist groups conduct cyberattacks to infiltrate, exploit, or destroy critical infrastructure to further
- threaten the national security of a country. Sometimes, terrorist groups attack globally to threaten international security altogether.
- compromise military equipment while disrupting military operations.
- disrupt the economy.
- cause mass casualties.
6) Malicious insiders/Internal collaborators
One of the most unexpected but highly used cyberthreat actors are malicious insiders or internal collaborators. Insiders can include employees (from administration to higher management), contractors, third-party vendors, or other business associates that have legitimate access to the company assets. A malicious insider or internal collaborator use this access to steal or destroy information for financial or personal gain. At times, malicious insiders work with third-party collaborators or cybercriminals to disrupt business operations and damage the organisation’s reputation.
7) Corporate spies
Lastly, corporate spies are another type of cyberthreat actors that you must know of. They conduct industrial or business espionage for either making a profit, disturb a competitor’s business by attacking crucial infrastructure, stealing trade secrets, and so on.
Emerging cyberattacks to look out for
As per various reports, the global average cost of data breaches estimates to approximately USD 4 million while the estimated annual losses reached USD 6 trillion in 2021. It has been estimated that cybercrime will increase at least by 76% by 2024. Along with the types of cyberattacks mentioned above, some new, more notorious ones are emerging in recent times. Here are the seven emerging cyberthreats to look out for –
1) Pandemic-related attacks
The period from 2020-2022 was a difficult one for the world. With COVID-19 pandemic hitting the world, economy, normal life – everything was difficult to deal with. However, for cybercriminals, it was an opportunity to attack networks and systems for their personal gains. Today, when the pandemic has slowed down and normalcy has come back, cybercriminals continue to leverage the pandemic and its related topics as backgrounds for their phishing and social engineering campaigns. They lure users with information that are in line with significant pandemic events like announcement of a new vaccine, sudden surge in cases, etc., with malicious links. Users, thinking the details are legit, click on the link, which leads to the installation of malware in the system, giving hackers the access, they need. Therefore, always double check such information with the authorised and Government websites of your country; make sure to check the email address thoroughly to ensure it is a legitimate one.
2) Cloud breaches
The cloud is one of the most amazing things that could have happened to the industry as it can store huge amounts of data and has many other benefits. However, as more companies are migrating to the cloud for facilitating remote working and business continuity, cybercriminals have gotten a new method of conducting data breaches and cyberattacks by targeting the cloud. They exploit threats like insecure APIs, access management, misconfigured storage, and data leaks. As per a report by VentureBeat, it was found that 94% of the companies experienced API cyberattack incidents in 2021. Apart from this, other threats like incomplete data deletion, legacy data, and vulnerable cloud apps are being exploited by the cybercriminals. Hence, ensuring that the data deletion process is accurate and complete, and that legacy data are decommissioned on time are crucial to prevent such cloud-based cyberattacks.
3) IoT attacks
Ever thought how the Internet of Things can become vulnerable that cybercriminals can attack them for their malevolent objectives? Well, most Internet of Things (IoT) devices may lack solid security features that puts them at risk of cyberattacks. Cybercriminals leverage those IoT vulnerabilities to gain control of devices that further helps them use botnets and infiltrate the network. That said, cybercriminals are now turning malware attacks to becoming more covert by targeting Internet of Things (IoT) devices and platforms. Last year, approximately 75% of organisations were under IoT malware attacks, spreading from one employee to another – rising the number of malware attacks to approximately 10.4 million per year.
4) Mobile security threats
Yet another emerging cyberattack technique that you must know of are the mobile security threats. During and after the pandemic, work from home and hybrid culture have been implemented, keeping the safety of employees in mind. However, working from home means the usage of networks that are not properly secured, patched, and managed by the IT security of your organisation. Adding to this, sometimes employees also use their smartphones, iPads, or tablets to maybe join a meeting or quickly get some work done. Cybercriminals take benefit out of it and exploit the unique IT security threats and vulnerabilities, which not only puts the individual at risk but also makes the entire organisation vulnerable to cyberattacks. While a robust solution for this is yet to be discovered, it is advisable to stick to one network, and get your iPads or tablets checked and authorised by your IT department while working from home.
5) Cryptojacking
Cryptocurrencies are one of the trending topics amongst most young people nowadays – especially Bitcoin. However, there are approximately 3000 other cryptocurrencies, most of which remain virtual. These virtual currencies use a distributed database known as blockchain for its operation. These blockchains are updated regularly with the information about the transactions. For production of new blocks, cryptocurrencies need computing power, and those who provide them are known as miners. This activity requires vast amounts of electricity; the Bitcoin network currently uses more than 73TWh of energy per year. This is where Cryptojacking comes into play.
Cryptojacking, also known as Cryptomining, is a cyberthreat that embeds itself within computer systems or mobile devices, using it to resources for mining cryptocurrencies. Cybercriminals who conduct this activity are known as cryptojackers, who hack into devices or systems to install a Cryptojacking software. The software operates in the background by mining or stealing from cryptocurrency wallets, without coming in suspect of the victims. Cryptojackers follow two primary methods to get a victim’s device to mine cryptocurrencies –
1. By infecting a website or online advertisement with a JavaScript code that can auto-execute once it loads on the victim’s browser.
2. By luring the victim to click on a malicious link in an email or online platforms that loads a Cryptomining code on the computer.
Sometimes, cryptojackers use both the methods to maximise their gains. As per a survey report by Kaspersky, Cryptojacking has grown approximately by 230% in the last one year. Victims usually cannot suspect the Cryptojacking software as they operate discreetly. However, if your system experiences frequent lags and slower performance, you might want to get it checked for malicious software operating in the background.
6) Cyber Crime-as-a-Service (CCaaS)
You have heard about Software-as-a-Service (SaaS) or Platform-as-a-Service (PaaS), right? But did you hear about Cyber Crime-as-a-Service (CCaaS)? This is one of the quickly emerging cyberthreats in 2023. Cybercriminals and threat actors with years of expertise have developed sophisticated services or tools that are then sold to other cybercriminals. There has already been a surge in cyberattacks with this Cyber Crime-as-a-Service attack, which is, unfortunately, becoming more of a commodity and expected to rise at unprecedented levels in the future.
7) Supply chain attacks
Last but not the least, supply chain attacks are yet another emerging cyberthreats that are even anticipated to rise in the coming years. Supply chain attacks targets an organisation through vulnerabilities in its supply chain. The vulnerabilities are usually linked to vendors that have poor security practices. As per the UK government data, 13% of companies regularly review the risks that their immediate suppliers have due to weaker security. These attacks disrupt the operations severely as commodities move from one location to another. However, it is surprising to see that very few organisations are aware of the potential cyberthreats that come working with suppliers or third-party vendors. Cybercriminals leverage this to their benefit and launch supply chain attacks to achieve their malicious objectives.
Legacy system decommissioning: A way to prevent cyberattacks
Recently, the DNA of approximately 2.1 million people were hacked due to a preventable negligence. It was a ransomware cyberattack, where the network of DNA Diagnostics Centre (DDC) – an American healthcare organisation, was infiltrated using a software called Cobalt Strike. It got hold of the databases that enabled the hacker to access millions of personal data. What’s more interesting was the software turned out to be the same on that cybersecurity experts use to tests system resistance. Unfortunately, by the time the intrusion was detected, warnings and actions were too late. Overall, the results were substantial, resulting in reputational damage along with critical fines. Not to forget, the effect on the victims, whose personal and health data were disclosed.
We mentioned above that this cyberattack happened due to a preventable negligence – wondering what it could be? Well, you will be shocked to know that all the stolen data were legacy data, which were relayed to DDC when it acquired a smaller company in 2012. As a matter of fact, DDC said that it did not have the faintest idea that such data was stored in its server.
Often massive companies have humongous amounts of data, which they often forget about. This turns into legacy data that are vulnerable to cyberthreats, as can be seen from the scenario above. That said, sometimes, legacy systems are also a part of companies, which again, are vulnerable to security threats. Isolating obsolete legacy system to keep them from cyberattacks is technically difficult to implement and costly. Hence the most reasonable way to maintain access to legacy data is to protect your company by decommissioning legacy systems.
But how do you do that? Well, TJC Group has developed a cloud-based application – Enterprise Legacy System Application or ELSA to help organisations decommission legacy systems.
ELSA is an SAP-certified application that is built on the SAP Business Technology Platform (BTP), ensuring that legacy data is decommissioned and stored securely. It also enables authorised users to re-access the data both before and after migrating to SAP S/4HANA or another ERP systems. A feature of ELSA is that even though it is built on SAP BTP, ELSA can decommission both SAP and non-SAP systems. Along with this, it can be delivered on-premises through SAP BTP or as Software-as-a-Service (SaaS).

A word from the Director of IT Security, TJC Group
Enterprise Resource Planning (ERP) systems, crucial for operations, serve as the backbone of businesses, orchestrating diverse processes for efficiency. However, as these systems centralize vast amounts of critical data and connect with other operational components of the information system, the importance of robust Cybersecurity measures becomes paramount. With an ever-evolving landscape of cyber threats, ERP systems can potentially be vulnerable points of entry for malicious actors, making it imperative to establish multi-layered defences.
Due to the large amount of important data held and the numerous connections with other components of the information system, the security of the ERP is vital for the company.
Integrating processes and data, ERP platforms streamline complex workflows, enhancing productivity and decision-making. Yet, this interconnectedness also exposes organizations to cyber risks, necessitating proactive strategies like regular security audits, encryption, and employee training for examples. By diligently fortifying ERP systems with Cybersecurity practices, companies can harness the full power of digital integration while shielding themselves from the potentially devastating impacts of data breaches and cyberattacks.
Severity of the cyberattacks
Irrespective of whether you are a startup, multinational company, a government institution, or healthcare provider, cyberthreat landscape is constantly evolving, with newer cyberattack methods emerging as mentioned above. Statistically, as per record, the United Kingdom has lost more than 34.5 million Euros due to fraud, cybercrime, and pandemic-related scams in 2021. The GCHQ National Cyber Security Centre (NCSC) responded to 723 cyberattack incidents, out of which, 200 incidents were pandemic related. At present, 300+ cybercrimes have been reported by CompariTech – which maybe even more, given that many cybercrimes go unreported. It has been estimated that by 2025, global cybercrime damages could account up to USD 10.5 trillion.
The impact of cyberattacks on organisations are severe; the aftereffects can result in –
- Reputational damage
- Financial losses
- Fine imposition
- Productivity and morale
- Business continuity
- Partnerships; loss of client trust.
- Restructuring
- Legal liability
Best practices to follow
Some businesses are more vulnerable to cyberattacks, majorly due to the nature of their industry and service. For example, financial institutions are more prone than legal firms or education institutions. However, that certainly doesn’t mean that industry-specific assets are risk-free. It is essential to take measures that can help create awareness amongst employees about cyberattacks and how to respond to them – if not prevented entirely. Some of the best practices that organisations can follow are –
- Creating an insider threat program.
- Training employees.
- Maintaining compliance.
- Regularly updating software and systems.
- Initiating phishing simulations.
- Securing site with https.
- Backing up business data.
- Continuous Improving regarding results of pen tests, audits, etc.
- Sharing experience with fellow company and authorities.
Key takeaways
- We, at TJC Group, take security very seriously. Our in-house cybersecurity experts make it a point to keep our employees updated and informed about cyberthreats and necessary precautions to be taken to make the systems safer and secure.
- That said, we take our client’s security sincerely as well. There are policies in place to systems and networks secure along with the applications we are developing.
- One of the most important steps to ensuring protection against cyberattacks is legacy system decommissioning.
- Ensure your legacy systems are properly managed to prevent attacks coming through vulnerable systems.
Connect with TJC Group today to decommission your legacy systems with ELSA and secure your data and organisation from unprecedented cyberattacks.







